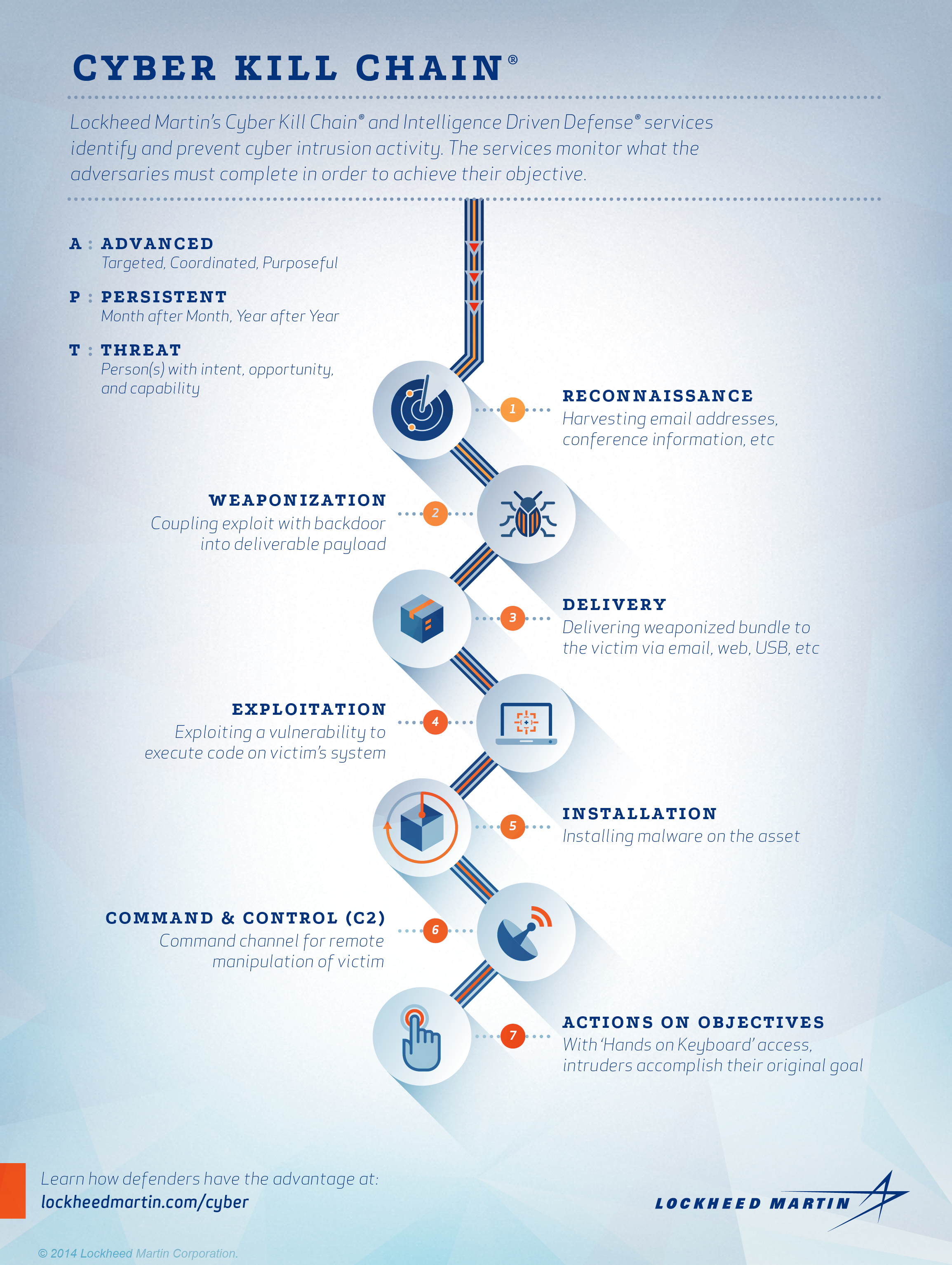
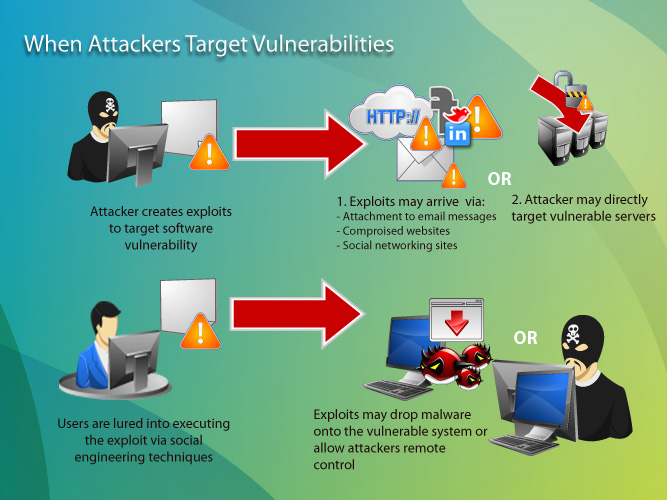
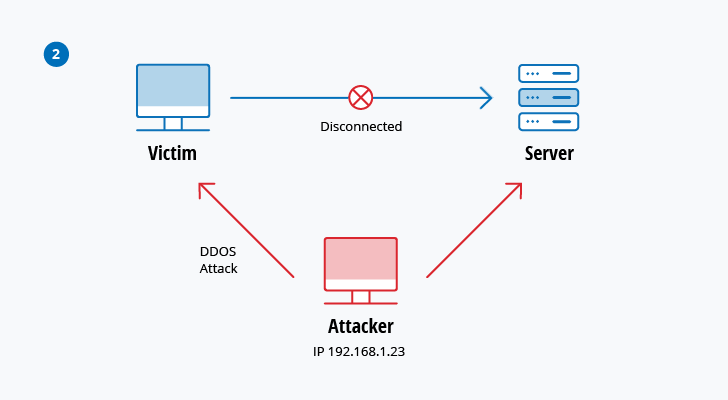
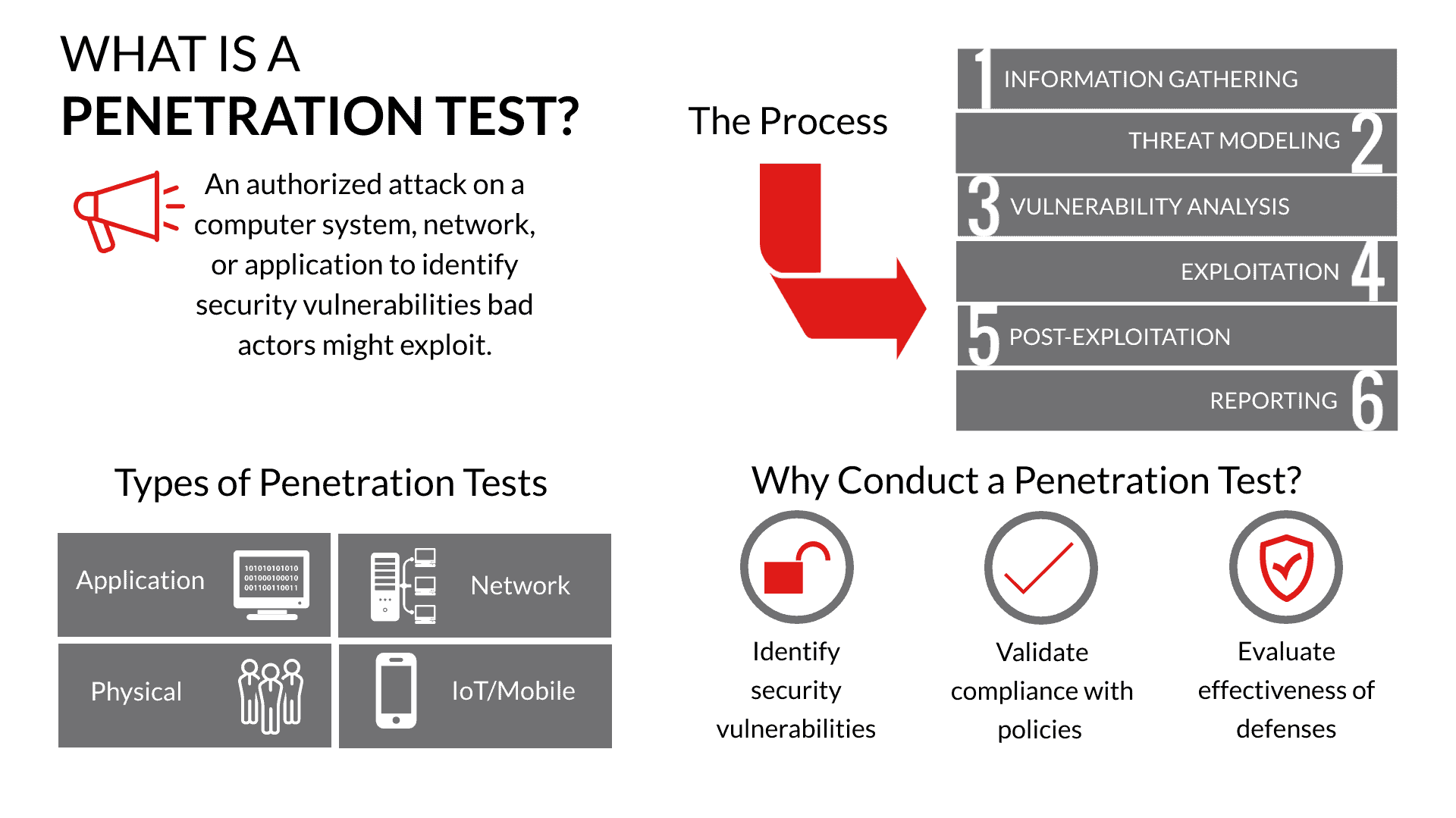
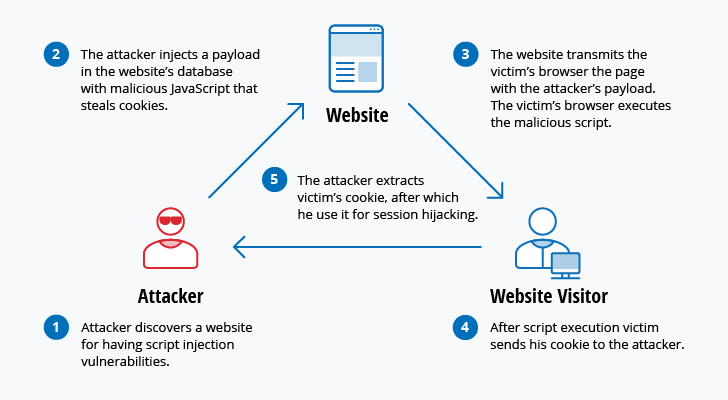
Michael J Myers Emerging Roles Of Combat Communication Squadrons In Cyber Warfare As Related To Computer Network Attack Defense And Exploitation by Michael J Myers | Willowbrook Shopping Centre

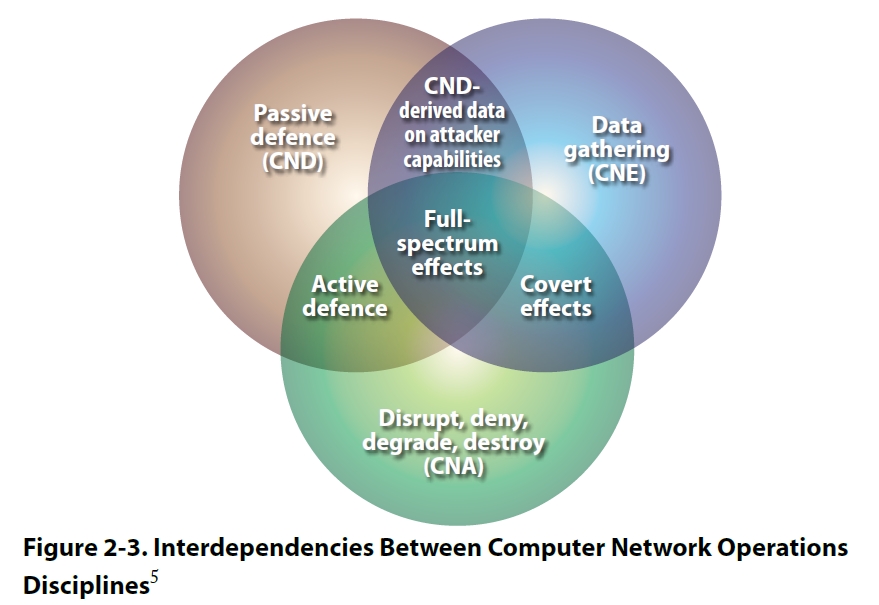
A schematic view of how Computer Network Attack (CNA)/ Computer Network... | Download Scientific Diagram

People's Republic of China Cyber Warfare and Computer Network Exploitation Capability Report | Public Intelligence
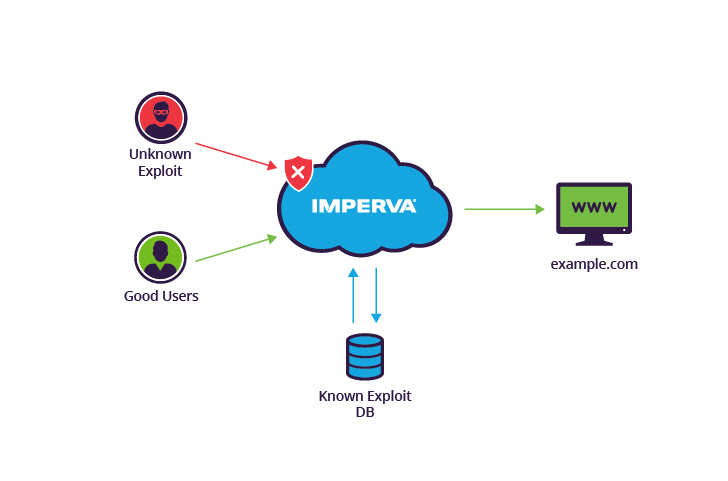
Example: Exploiting a typical Windows Domain network - Bob's Tech Talk - Bobs Tech Talk News and Reviews



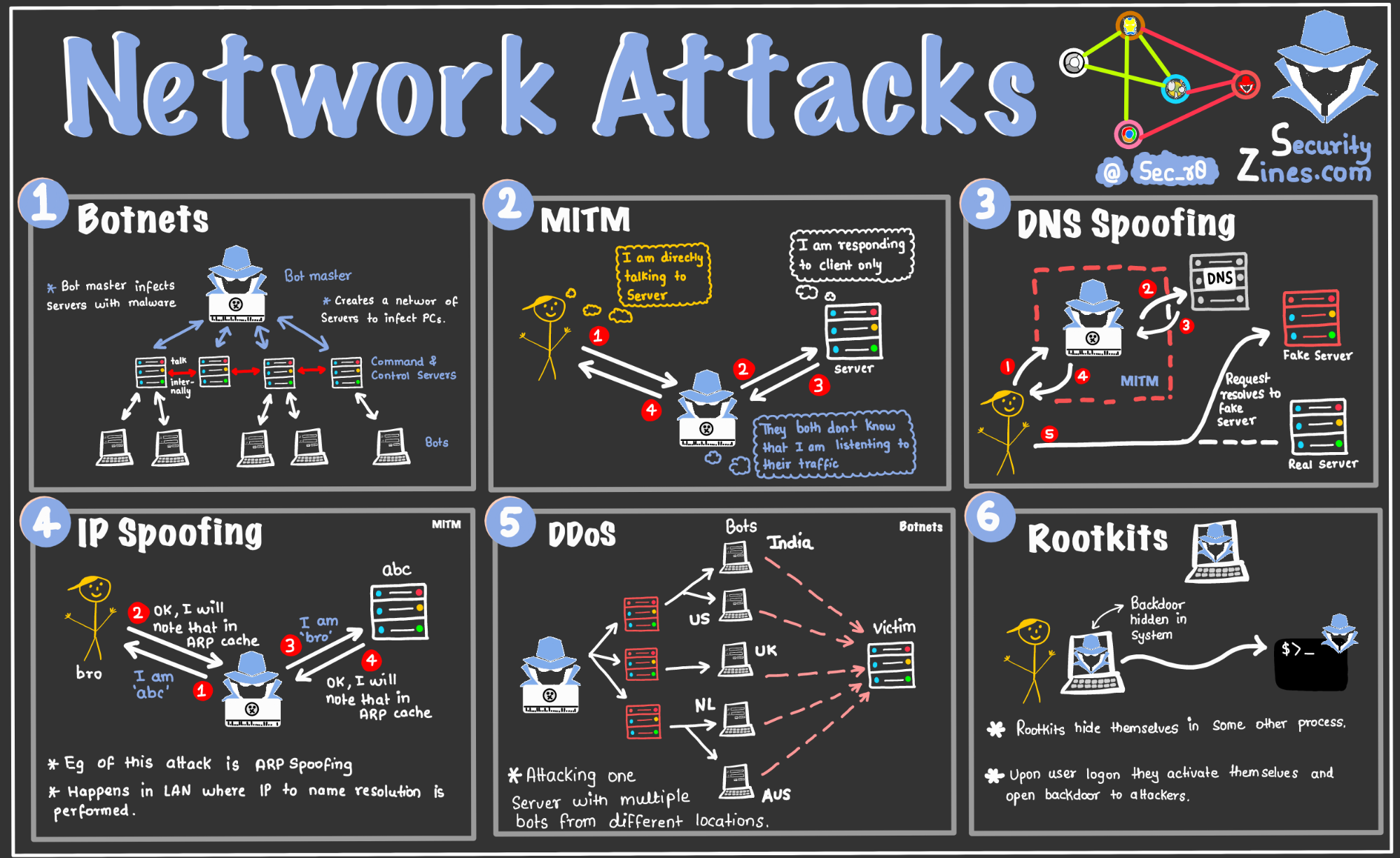


/cloudfront-ap-southeast-2.images.arcpublishing.com/nzme/KTYPA66EVVGTLICWV2IJP2OS4U.jpg)